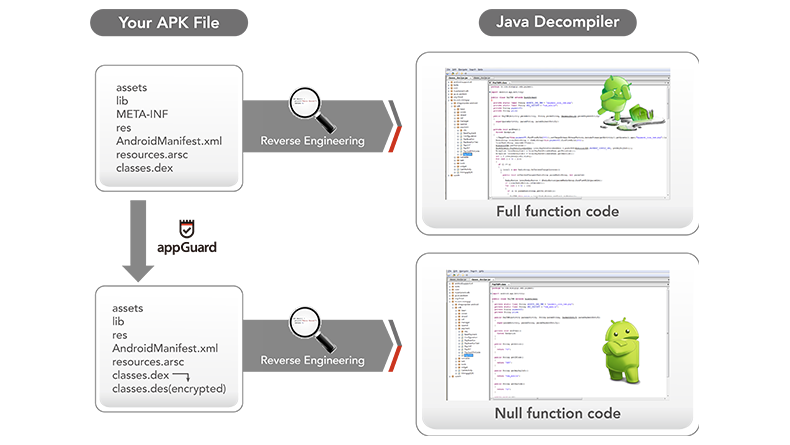
01 Anti-Reverse Engineering
Protect the security of various app codes (dex, so, dll, etc.) and block decompilation and disassembly tools.
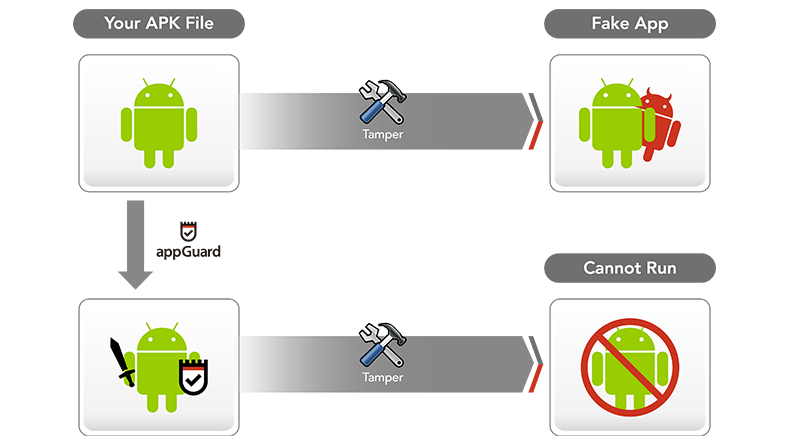
02 Anti-Tampering
Verify the integrity of the app to prevent pirated, cracked, or modified versions.
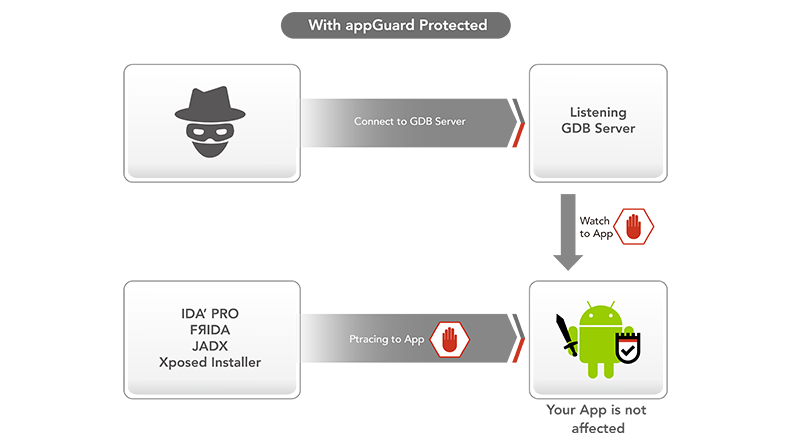
03 Anti-Debugging and Cheating Tools
Detect Android debugging and cheating tools in real-time to avoid app tracking, interception, or injection. Ensure execution logic remains undisturbed and intact.
04 Storage Encryption
Encrypt app data or runtime-generated data, binding it to devices to prevent unauthorized modification or theft.
OWASP Mobile Top 10 Risks
-
App Integrity Protection
- Prevent source code theft and misuse, protecting brand reputation.
- Ensure the confidentiality of stored data.
- Safeguard intellectual property rights of app creators.
-
Prevent Malicious Program Intrusion
- Avoid the insertion of harmful programs that could cause irreparable damage.
- Extend the app’s lifecycle, particularly in the gaming industry.
- Reduce the workload of developers, allowing them to focus on new features.
What We Provide
-
01
Risk assessment reports during development or pre-launch, helping developers identify and resolve potential issues.
-
02
Automated protection system post-launch for seamless service.
-
03
Customizable protections tailored to specific APKs.
-
04
Up-to-date protection technology with continuous updates for the latest and most robust security features.
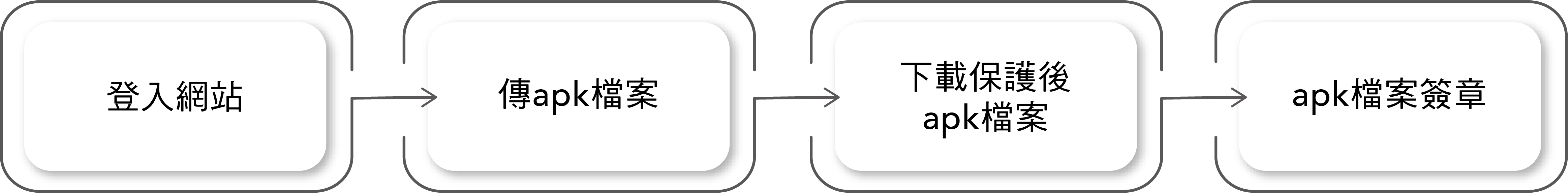
Android Protection Process
iOS Protection Process