Introduction
Simulate actual phishing emails to check user security awareness.
Along with educational training to raise employees' security awareness, reduce the relative risk of social engineering attacks.
Service Features
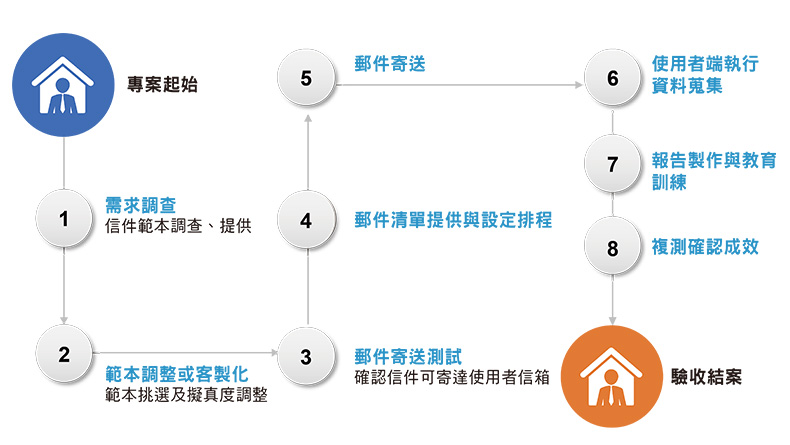
Project Execution Process