4 Key Steps to Block Advanced Attacks
In combination with minimum permission and program control, this will significantly reduce attacks and block malware-type attacks.
Automa
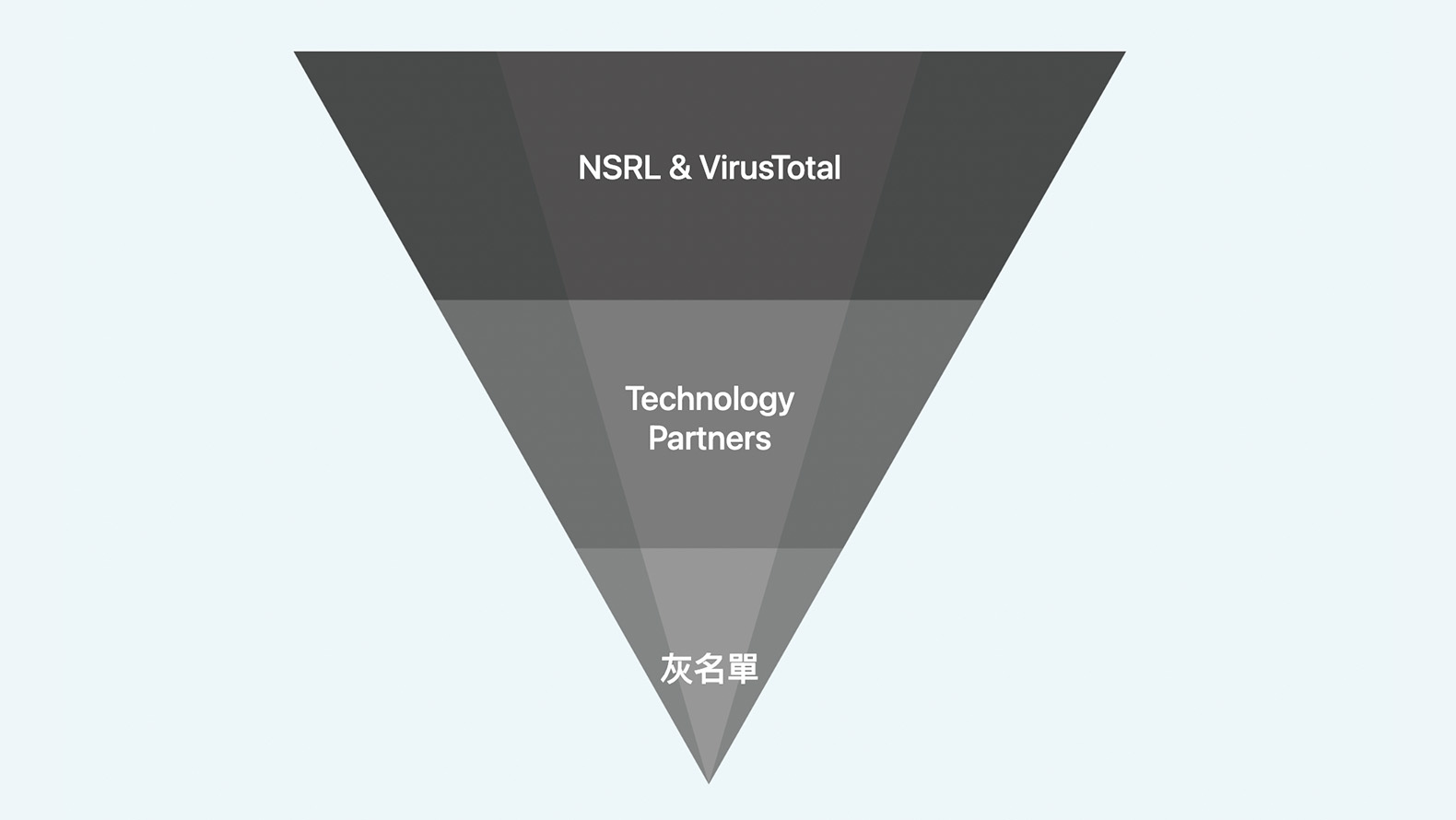
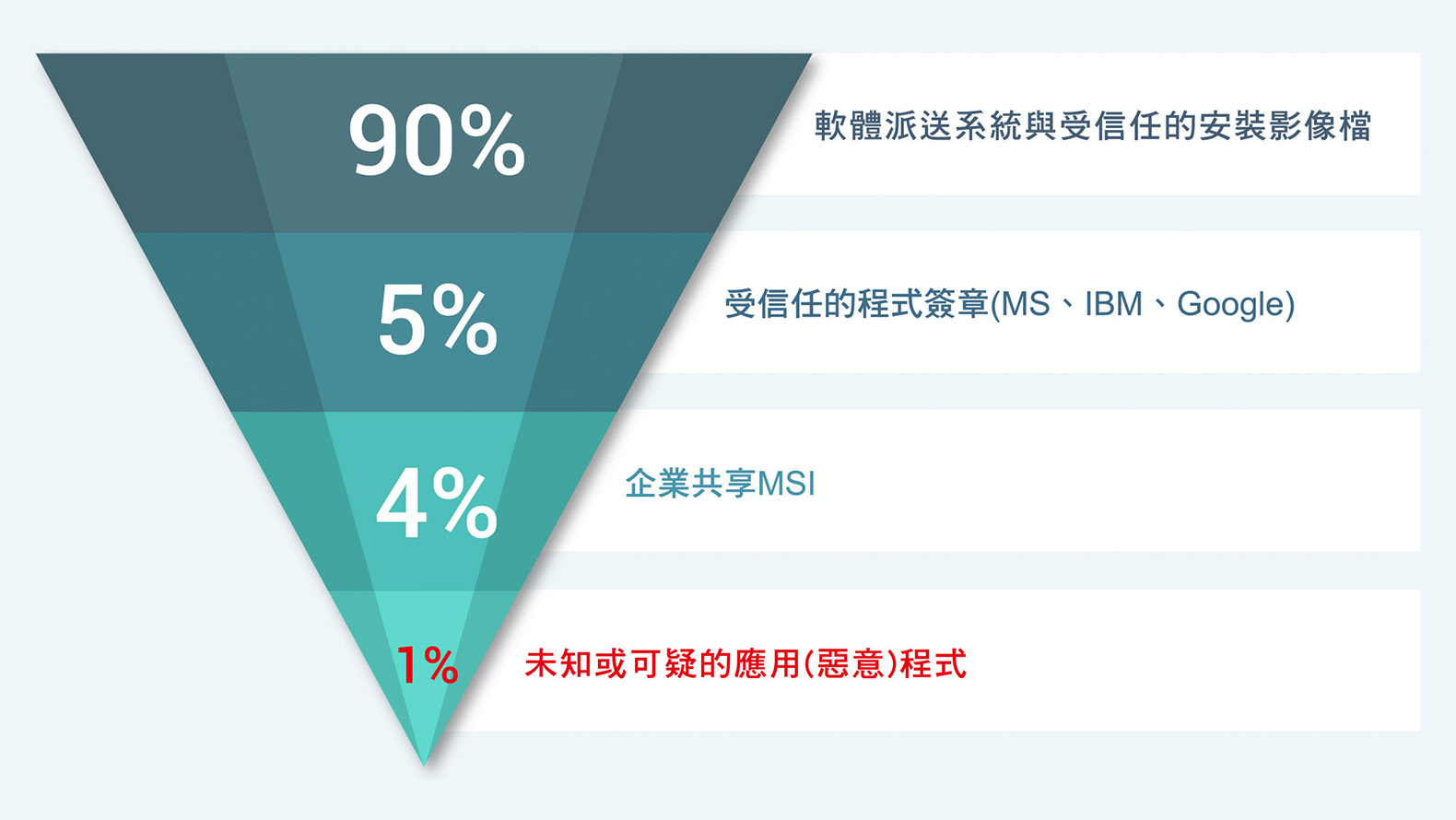
Establish trust policies, which will include 99% of the programs, and execute them automatically
- Will not affect user operations
- Intuitive linear deployment
- Effective ongoing management
- Accurate and reliable
Isolation mode
Identification and Remedy
- Obtain reputation score
- Block known malice; allow known goodwill
- Identify known sources and locations of all malware
- Block the distribution and access to network resources of malware