GTB DLP Data Loss Prevention
When enterprises send text files, spreadsheets, presentations, and database files, they sometimes contain "sensitive" or "proprietary" information (such as personal data, patents, etc.) that needs protection to prevent unauthorized transmission or leakage. Although most enterprises implement effective "outside-in" protection measures and management mechanisms, they often neglect "inside-out" data leakage, exposing the company to huge risks such as reputational damage, regulatory violations, loss of competitive advantage, early exposure of financial conditions, loss of customer trust, and damaged business partner relationships.
add Catalog DownloadProduct Features
Product Advantages
-
01
Protect Intellectual Property / Valuable Multimedia Content (trailers, movies, music files, photos, source code) in Any Data Format
-
02
Covers All Network Ports, All TCP Channels (Including SSL)
-
03
100% Detection Rate, No False Negatives
-
04
Block Based on Severity Without the Need for a Proxy Server
-
05
Uses Multi-Field Policies to Protect Structured Data
Why Choose GTB
The GTB DLP solution differs from other major competitors in the market. Its unique features cover internal threats from both "trusted" and "untrusted" sources. GTB’s patented Data AccuMatch™ technology is the most precise and fast detection algorithm available. GTB’s Content-aware Reverse Firewall™ combines its advanced fingerprinting engine to detect all protocols (including unknown protocols) and prevent leakage, not just event reporting.
Protect Sensitive Company Data, GTB Provides the Solution
-
GTB Inspector
Content-aware Reverse Firewall™, combined with its advanced fingerprinting engine, can accurately and quickly detect all communication protocols and immediately block data leakage. It covers all network ports and all TCP channels (including SSL) and all communication protocols, regardless of data format. GTB DLP protects confidential data and intellectual property/valuable multimedia content, such as trailers, movies, music files, photos, and source code, with 100% detection accuracy.
-
eDiscovery GTB
eDiscovery allows the discovery of confidential data on any user’s computer within the corporate network and performs data classification. It accurately monitors and reports violations of any document retention rules, saving system administrators time searching for and classifying confidential data.
-
Endpoint Protector
GTB’s endpoint protection prevents the output of protected confidential content to removable media devices in a content-aware manner. It can automatically encrypt and side-record the output of related confidential data. Supports both online and offline enterprise operation policies.
-
Users can encrypt and authorize important files themselves, or automatically encrypt and manage permissions for sensitive data identified by eDiscovery on computers, allowing users to only read or edit, restricting printing or screen capture, etc.
Management Platform Provided by GTB
The GTB DLP console provides unified management of gateway and endpoint information, effectively classifying sensitive information, and centralizing policy settings for easy and effective management of all GTB DLP modules.
GTB Offers You the Best Service
GTB brings the latest generation of technology to prevent the loss of confidential and personal data and introduces groundbreaking innovation to the information security market. The product provides unprecedented real-time visibility and precise control, suitable for organizations of all sizes, with easy management and reasonable cost to effectively prevent data leakage, enforce corporate information security policies, and protect the company’s brand and reputation.
DataSunrise Database Security
DataSunrise Database Security Solution is a high-performance, real-time software that spans multiple platforms, designed to protect databases and their stored content in heterogeneous environments. Whether hosted in the cloud or on-premises, it safeguards the enterprise’s databases from external and internal threats, including SQL injection attacks and unauthorized access. The built-in DataSunrise Database Compliance Automation Engine and reporting features provide a comprehensive audit, protection, search, and high-performance data masking solution.
add Catalog DownloadProduct Features
Product Advantages
-
01
Regulatory Compliance
Role-based database security management policies. Automates compliance actions for regulations such as GDPR, HIPAA, SOX, PCI (or custom regulations).
-
02
Traffic Analysis
DataSunrise intercepts database traffic and performs intelligent analysis. It automates the process.
-
03
Intelligent Learning Engine
Role-based database security management policies. Automates compliance actions for regulations such as GDPR, HIPAA, SOX, PCI (or custom regulations).
Why Choose DataSunrise
Applicable to Various Types of Databases

RANDTRONICS Protect Sensitive Data
RANDTRONICS is the perfect solution to prevent potential internal data leakage. Only by encrypting sensitive data can regulatory compliance be ensured. The company’s data will be fully protected, eliminating concerns about the leakage of sensitive information.
add Catalog DownloadProduct Features
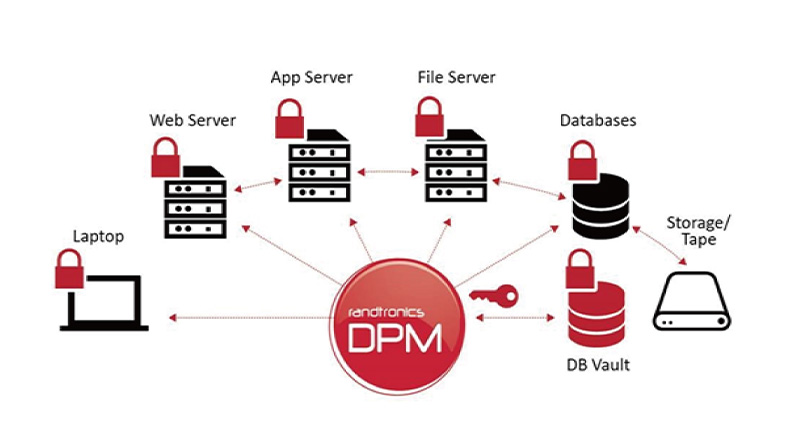
DPM (Data Privacy Manager)
DPM is a software solution developed by Randtronics that provides protection for files, applications, and databases without requiring any changes to the applications.
DPM is a data protection software solution that supports Windows & Linux (including virtual machine environments) and can protect both structured and unstructured data simultaneously. It provides encryption, tokenization, masking, and anonymization capabilities, allowing users to choose encryption keys and integrate with HSM.
-
01
easyCipher
Provides encryption and access control for files, directories, applications, and databases on laptops, desktops, and servers.
-
02
DPM easyData
Offers tokenization, encryption, and anonymization via a network service interface while creating masking policies for unauthorized access.
-
03
DPM easyKey
An independent key management module that can generate keys internally or through HSM.
-
04
DPM Database Manager
Provides column-level encryption for databases. Can be integrated with DPM easyData for tokenization, encryption, and anonymization.
DPM Server System Architecture
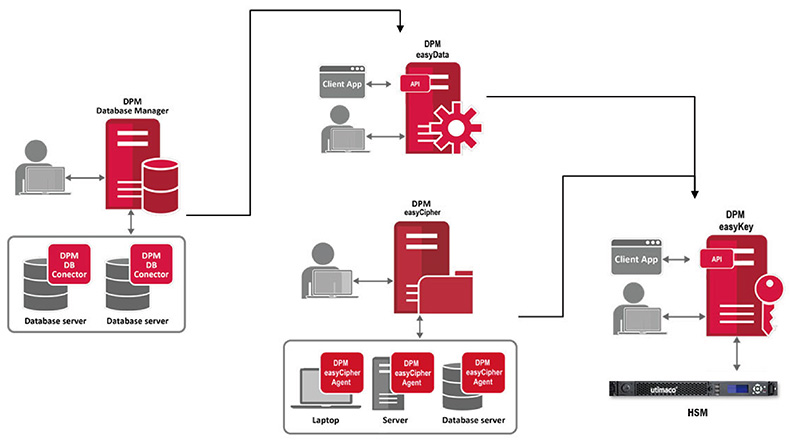
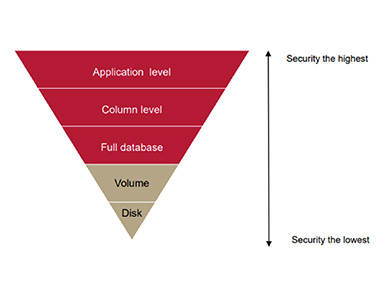
DPM modules can perform encryption at the application, database, and file system levels.
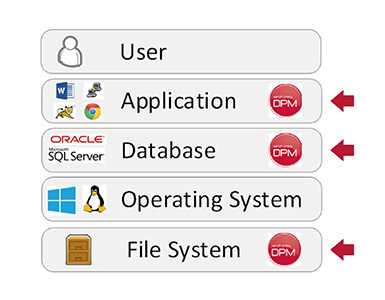
Encryption can be applied from the entire database down to the column level, and up to application encryption.
HSM Utimaco Hardware Encryption/Decryption Module
CryptoServer Se Series Gen2
Next-generation hardware encryption modules industry standard. Utimaco’s next-generation CryptoServer protects critical keys for various servers and application systems. It comes with integrated software support for industry standards (e.g., PKCS#11, Microsoft CSP/CNG, JCE, ...) suitable for most application scenarios such as financial transaction security, enterprise PKI integration, database encryption, etc. The next-generation CryptoServer Se-Series Gen2 offers two operational modes: PCIe interface card and network device. The computational speed can reach up to 10,000 RSA signatures per second or 6,000 ECDSA signatures per second (in bulk processing mode), with both PCIe cards and LAN Box versions available, suitable for common PC and server architectures, ideal for server centers.
add Catalog Downloadu.trust Anchor Se15k/Se40k
Utimaco’s highest-performance key protection encryption module pushes the encryption process to another level. Up to 40,000 signatures per second, RSA 2048 bits can reach up to 35,000 signatures per second. It also provides unlimited key storage space, offering excellent cost-performance to challenge industry leaders. The optimal choice for large data storage and encryption.
Low Operating Costs
- Provides high-performance at an attractive price
- Entry-level models available for low-performance applications
- Complete and detailed remote management functions, accessible via PinPad or Smartcards login
- Efficient key management and remote firmware updates
- Automated remote monitoring and diagnostics, supports SNMP protocol
- Software simulator provided for evaluation or integration testing
Features
- Key authorization API and tools (according to EN 419 221-5 protection principles)
- Tamper-resistant security
- Secure key storage and computation within the HSM’s secure boundary
- Secure key storage and computation
- Comprehensive key management functions
- Keys can be stored in the HSM or in encrypted files
- Smartcards can be used for high-strength identity authentication
- Supports "n out of m" identity authentication mechanism to encrypt and protect backup data (objects, keys, configuration files) with up to 16 people holding the MBK keys
- Role-based access control can be set for duty separation
- Remote management
- Supports OS: Windows 2016, Solaris 9, 10 (32/64-bit), Red Hat Enterprise Linux 8, SUSE Linux Enterprise Server 11, Debian 9 "Stretch"
Specifications
-
01
Supported Algorithms
- RSA, ECDSA with NIST and Brainpool curves
- ECDH with NIST and Brainpool curves
- AES
- CMAC, HMAC
- SHA-2 family, SHA-3
- Hash-based Deterministic Random Number Generator (DRG.4 acc. AIS 31)
- True random number generator (PTG.2 acc. AIS 31)
- Up to 3,000 RSA signature operations per second or 2,500 ECDSA signature operations per second (in bulk processing mode)
-
02
Application Programming Interfaces (API)
- PKCS#11
- ECDH with NIST and Brainpool curves
- Microsoft Cryptography Next Generation (CNG)
- Utimaco High-Performance Cryptographic Extended services Interface (CXI)
-
03
Network Device Hardware Specifications
- 1U height, 19” rack specification
- Built-in dual power supply redundancy, 100~240 V, 50~60 Hz AC 2 x 300 W
- Power consumption: average 45 W / 66 VA, max. 50 W / 70 VA
- Heat dissipation: max. 171 BTU/h
- 2 RJ45 1 Gb/s network interfaces
- Operating temperature: +10°C to +50°C (+50°F to +122°F)
- Storage temperature: -10°C to +55°C (+14°F to +131°F)
- Mean time between failures (MTBF): 100,000 hours at 25°C / 77°F, environment GB, GC - Ground Benign, Controlled

International Certifications and Environmental Certifications
- FIPS 140-2 Level 3*
- CE, FCC Class B
- UL, IEC/EN 60950-1
- CB certificate
- RoHS II, WEEE
Our Partners



