Endpoint protection: Defend, detect and respond to all threats
Cortex® XDRTM the world’s first expandable detection and response platform that collects and integrates all security data to block precision attacks. It can integrate defense, detection, investigation and response through a single platform to provide the best security and operation efficiency.
Cortex XDR got the highest level score for integrated detection and protection in the 3rd round of assessment by MITRE ATT&CK®, ensuring the security of data and leaving you carefree.
Why choose CORTEX XDR?
Prevent Attacks Using Comprehensive Visibility and Analytics
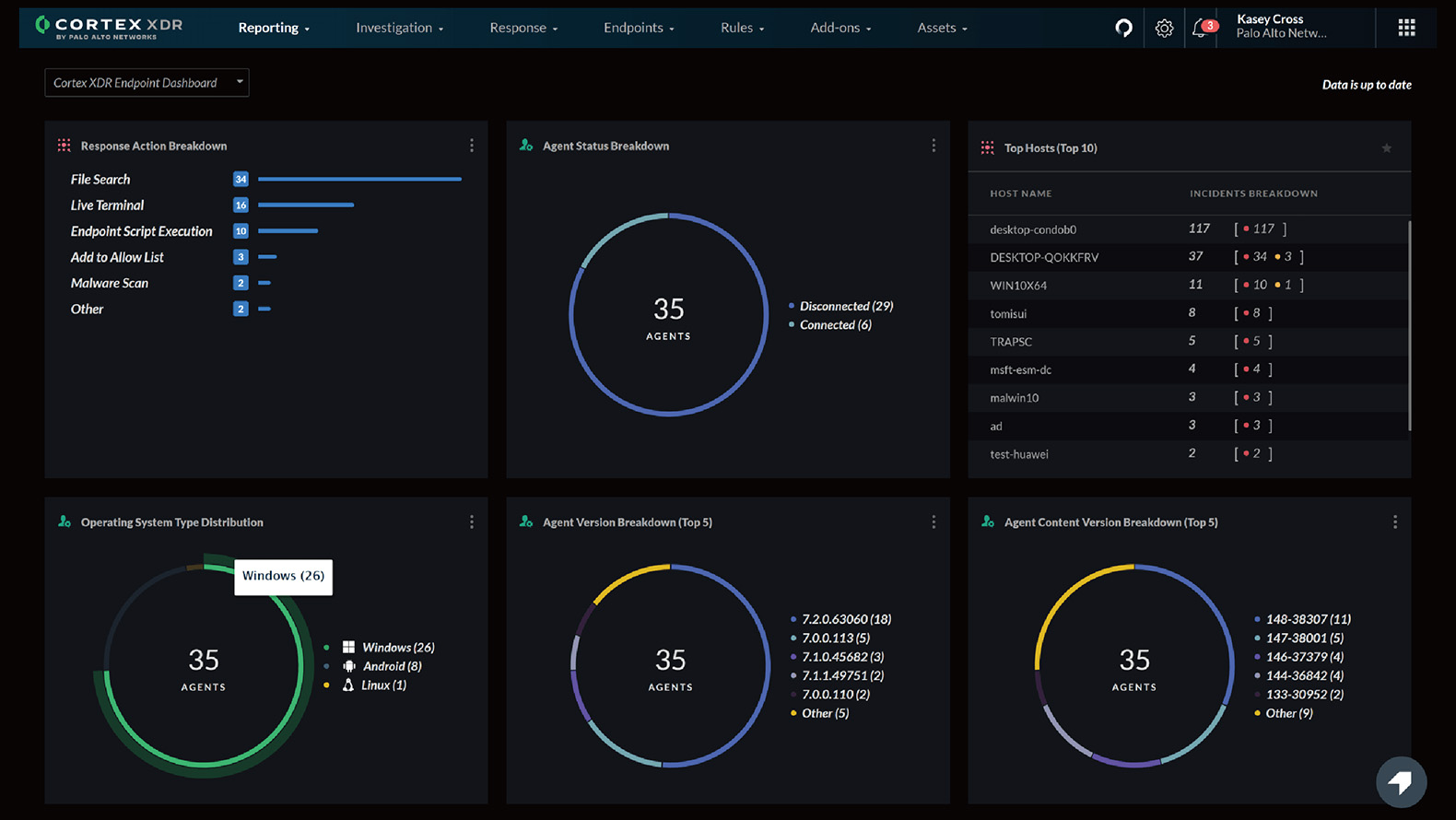
Improves the performance of information security protection for enterprises
Cortex® XDRTM powerful platform with intuitive display dashboard
-
Complete endpoint security
Protects your endpoint through NGAV, host firewall, disk encryption and USB device control.
-
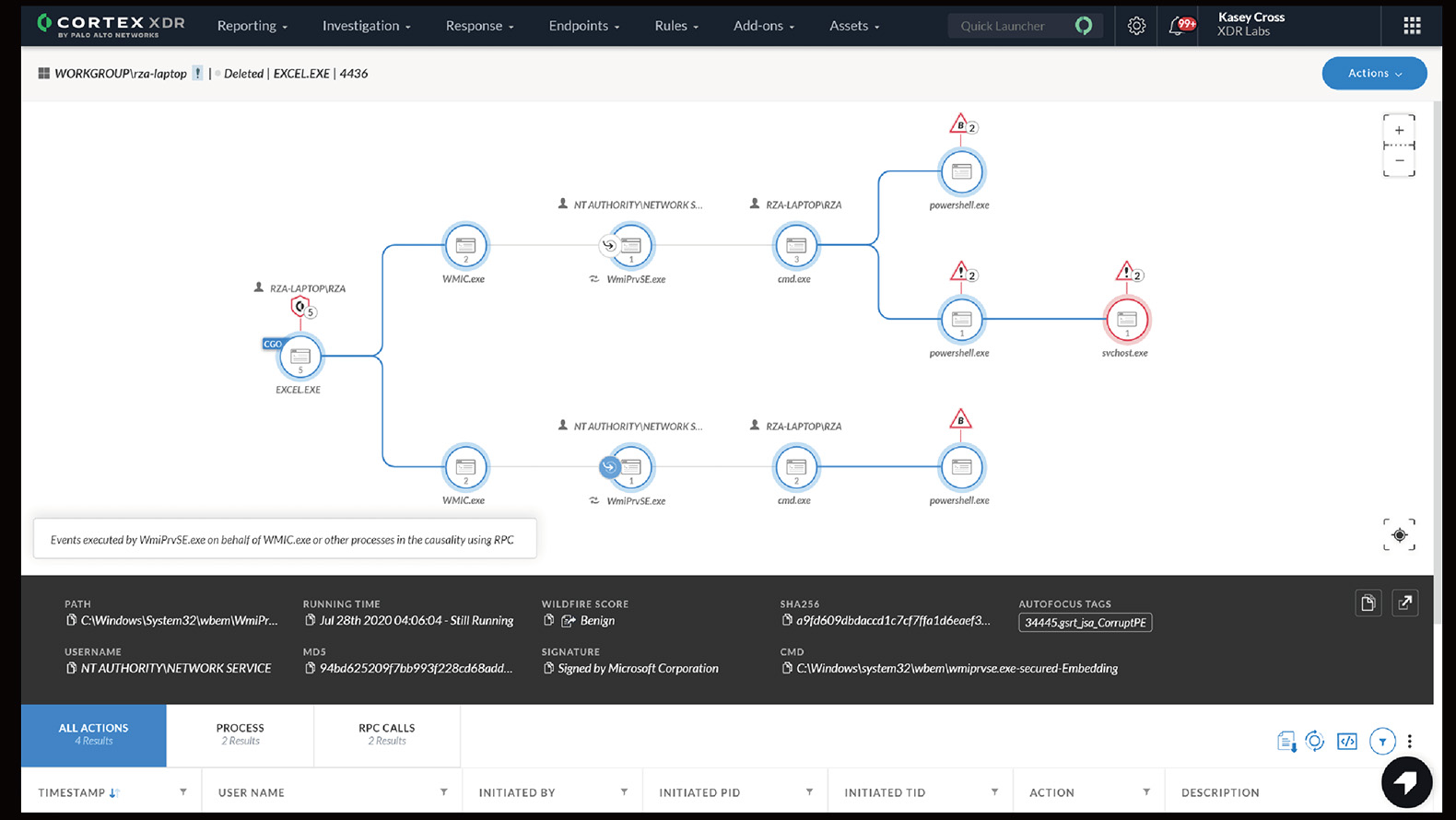
Machine learning driven threat detection
Uses behavior analysis to find hidden threats, such as abuse by internal personnel, credential attacks, malware and data leakage.
-
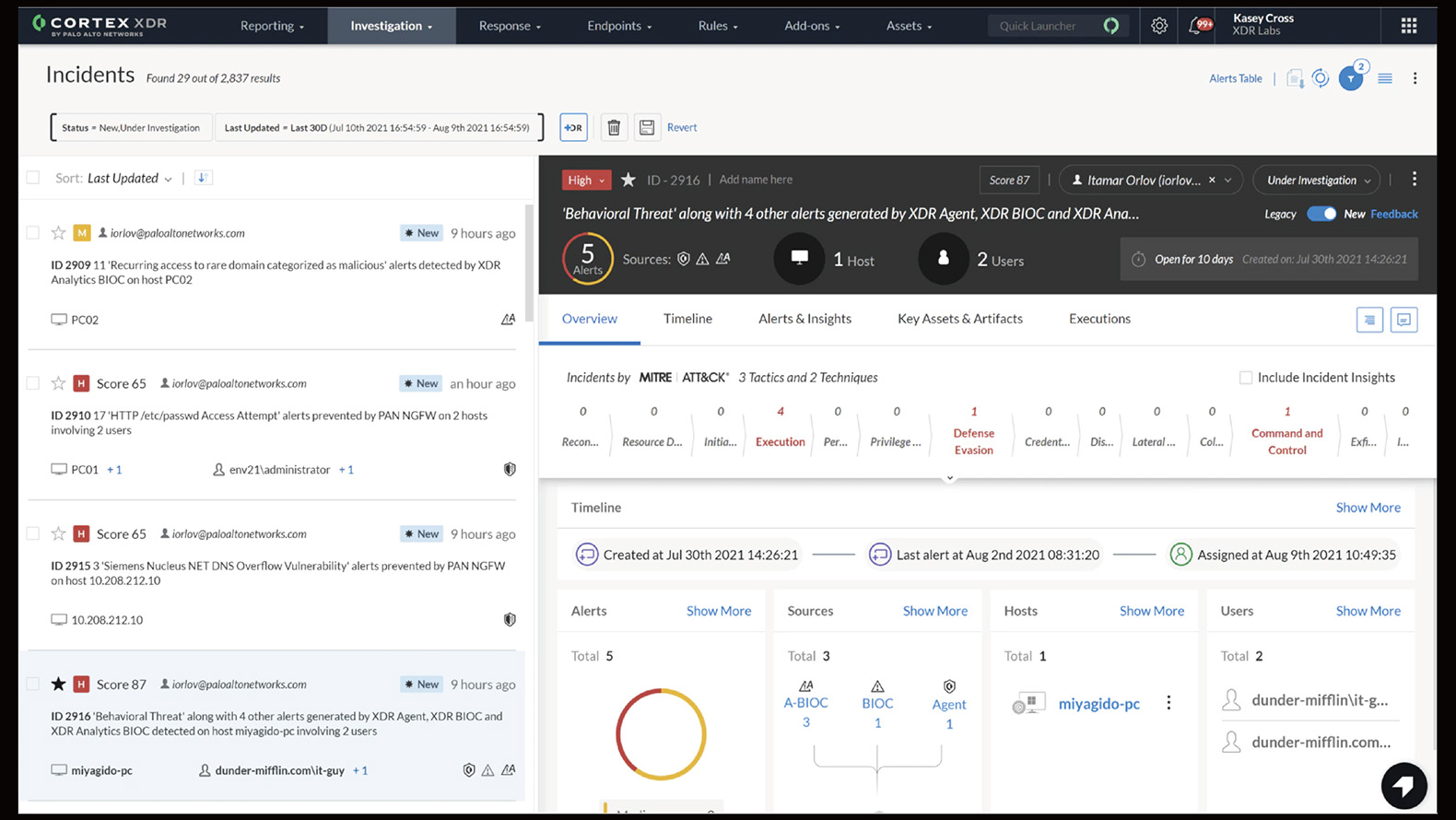
Incident management
Shorten investigation time through intelligence and warning grouping. Incident scoring allows you to focus on the really important threats.
-
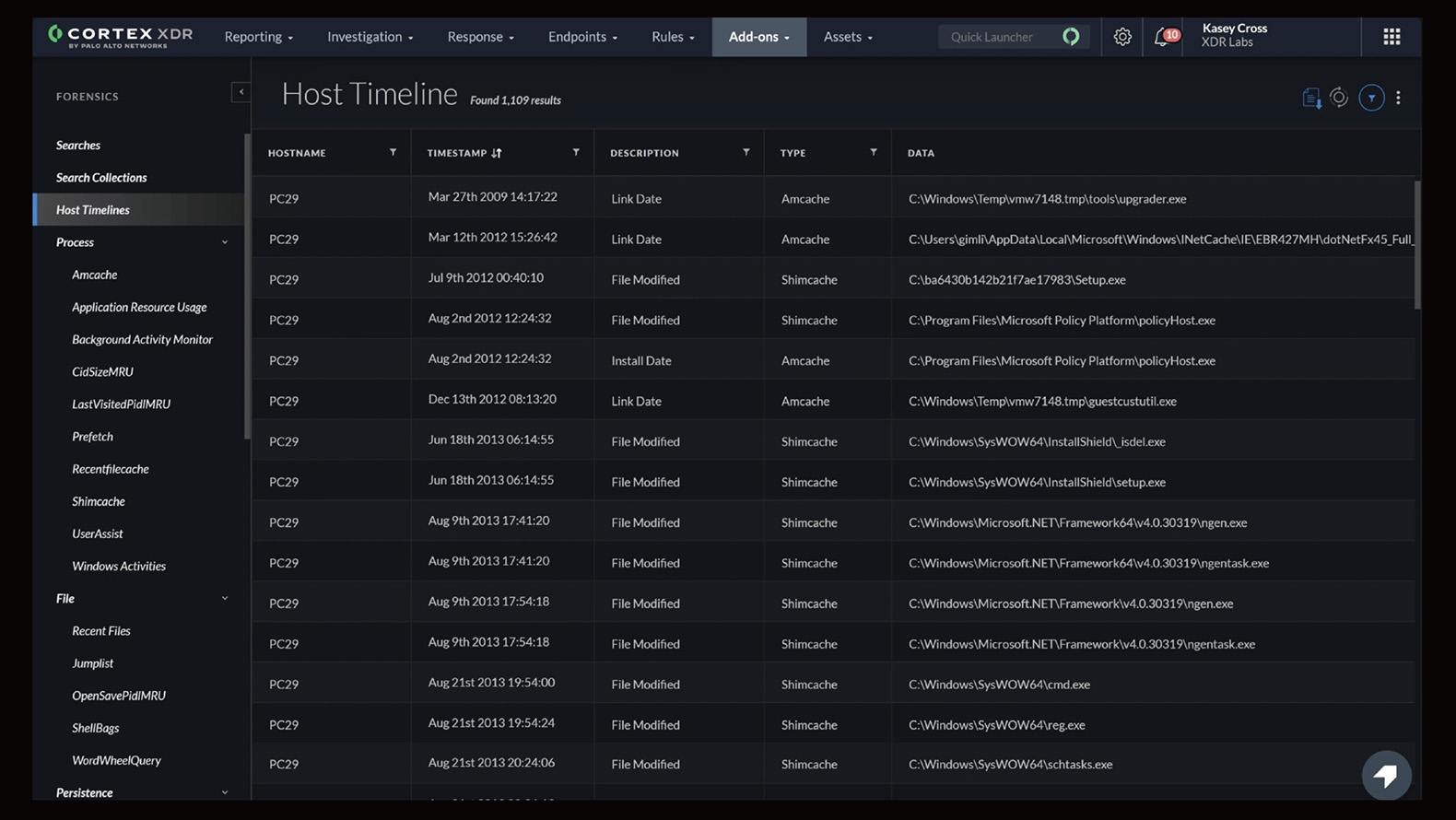
In-depth identification
Execute in-depth internal and regulatory investigations even if the endpoint is not connected to the Internet.
-
Flexible responses
Block attacks that are moving quickly, isolate endpoints, execute instruction codes or scan the entire environment to stop the threat in real-time.