Why is there the need to import information and communication security management systems?
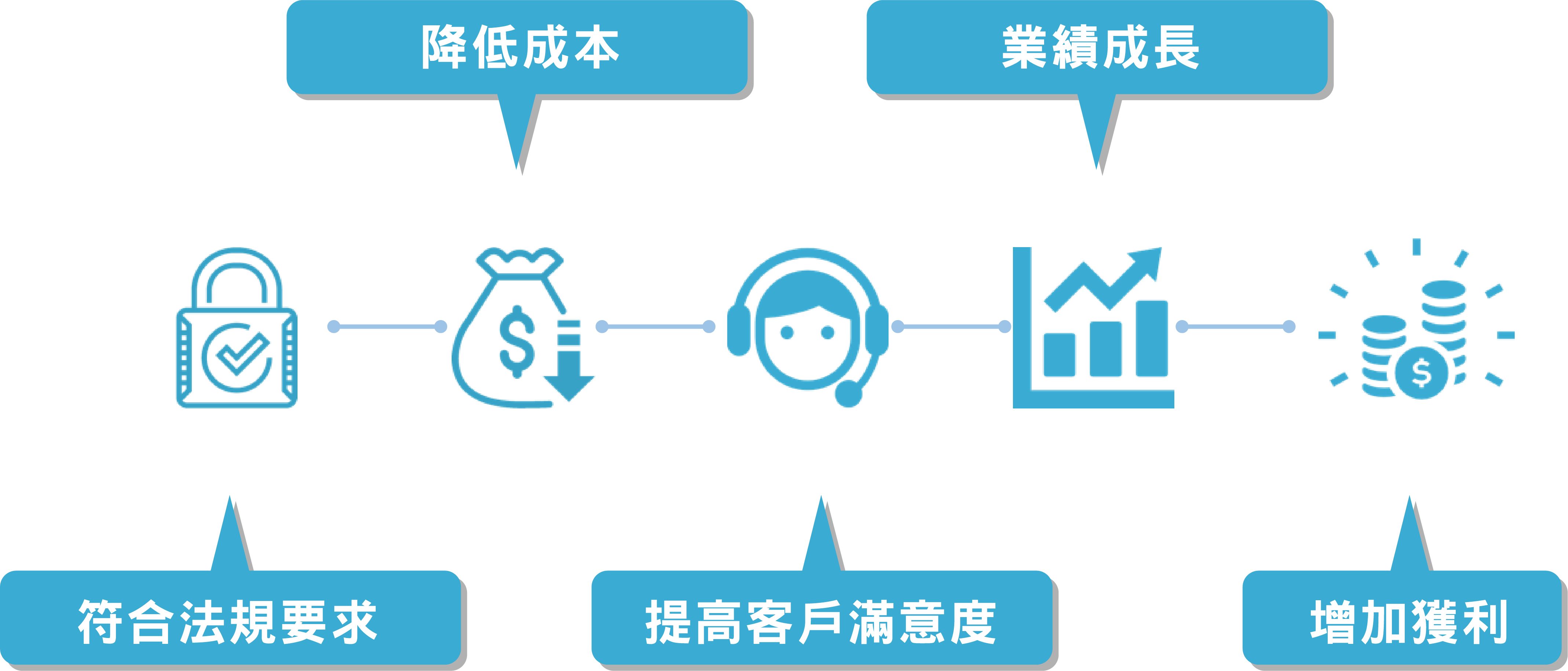
Life cycle of information and communication security management system – using ISMS as an example
.Backup as required by ISO 27001 (backup) - IDC services.Technical vulnerability management - PT/VA/Cybersecurity health check.Providing integrated information security services and panoramic planning
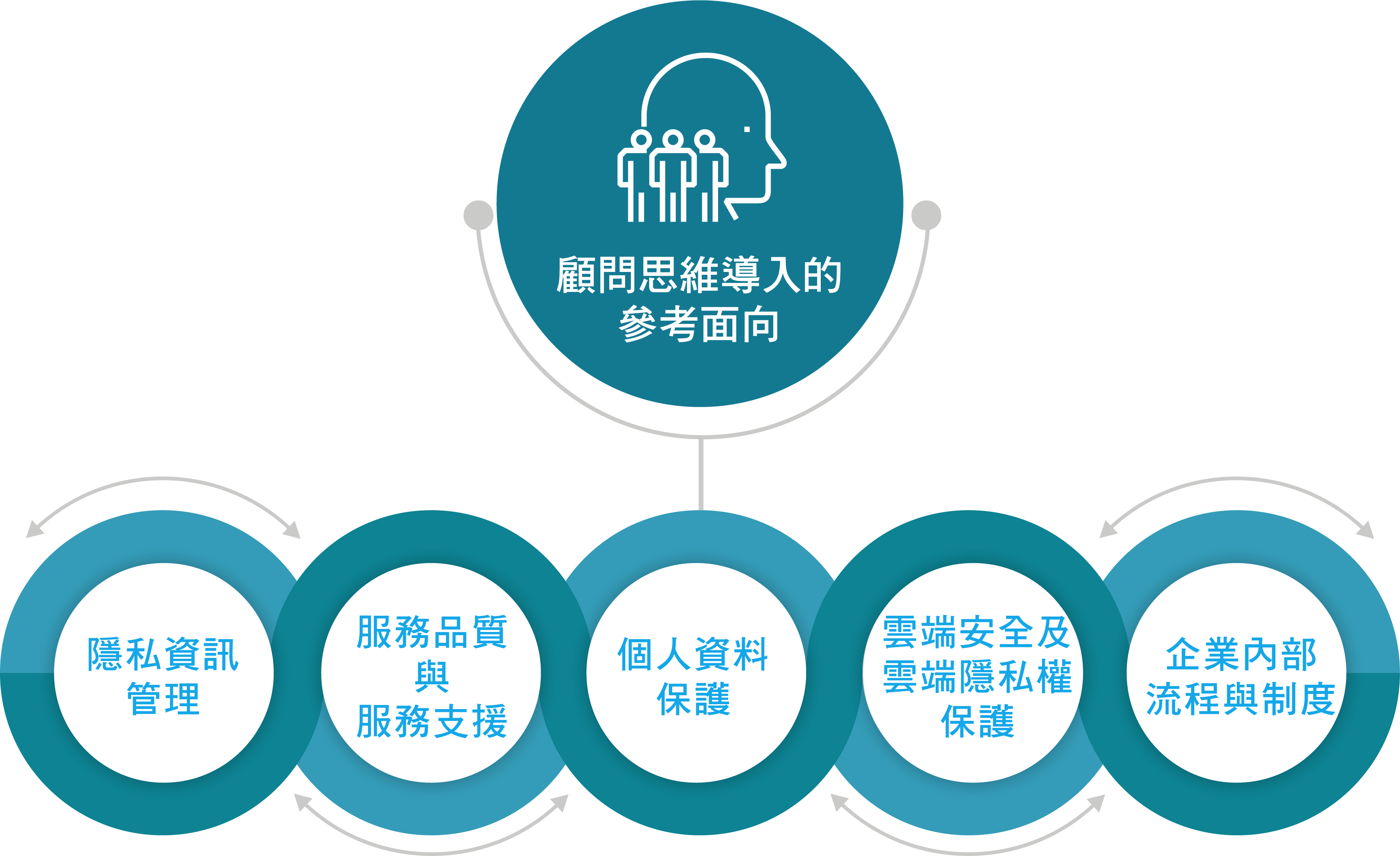
Aspects of consideration for the introduction of ISMS
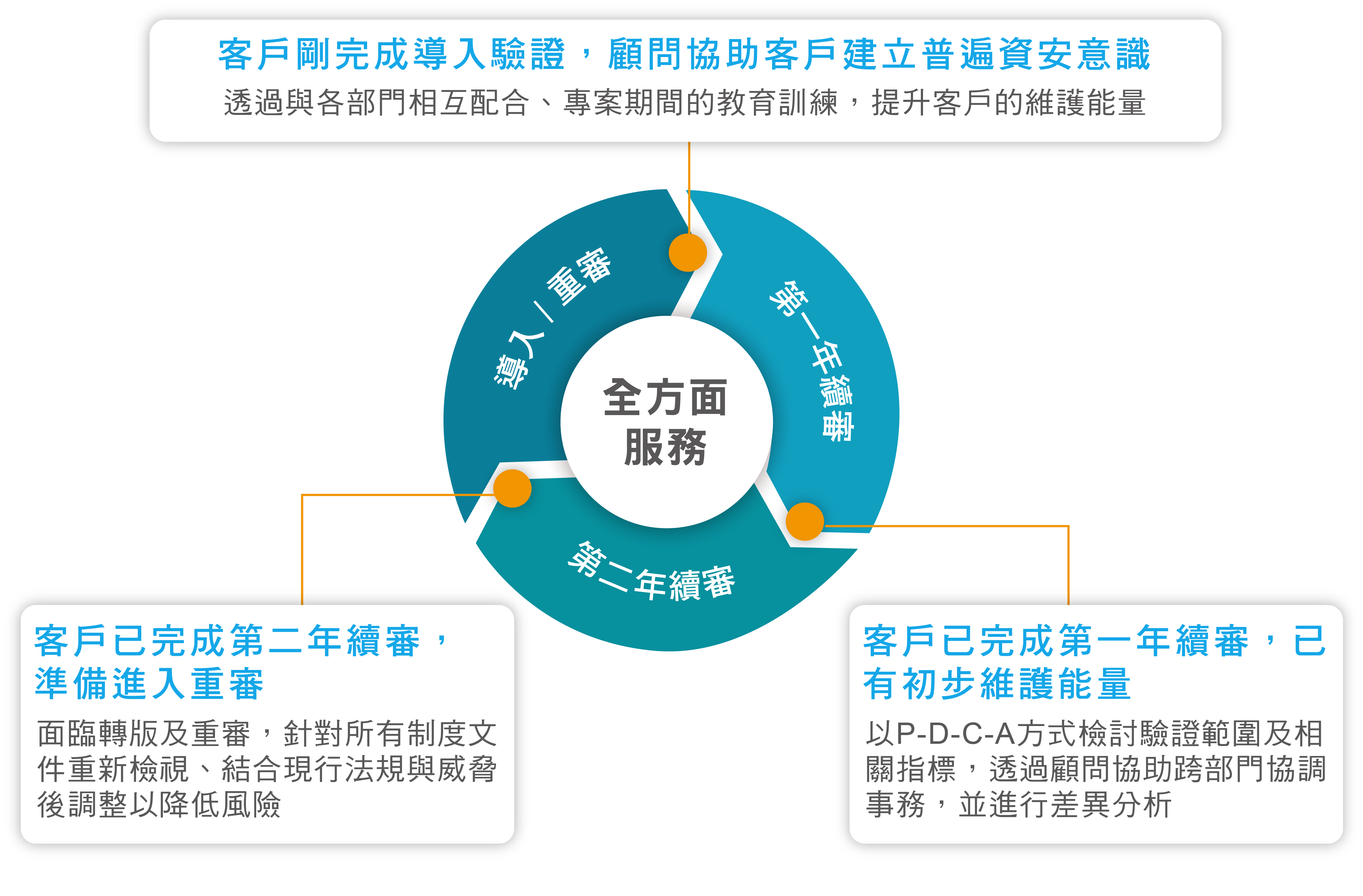
Modularized service for information and communication security management systems
Service modules can be provided according to the actual internal needs of the clients after dismantling the introduction process
-
01
Risk assessment and improvement plan consultation
-
02
Assistance with preparation and convening of the management review meeting
-
03
Business continuity plan subject drills
-
04
Information asset inventory
-
05
Cybersecurity training and education
-
06
Other consultation services (calculated in person-days)
-
07
Internal cybersecurity audits and external audit accompaniment
-
08
System document recommendations and adjustments
Why choose gamania CloudForce?


Valid information security certificates of gamania CloudForce

Valid information security certificates of gamania CloudForce
Advantages of gamania CloudForce
-
01
gamania CloudForce is a local business; in addition to its own products and information security services, it is also an agent of leading global information security products, providing clients with the best practices around the world
-
02
Members of the consulting team have worked as risk management information security consultants in large enterprises and well-known accounting firms with years of experience
-
03
Information security policies and frameworks from a panoramic analysis, and provide comprehensive information security integrated services
-
04
Flexible and safe project contents not only introduce the policy management aspect. Actual technical services for information security operation can also be provided to clients for both internal and external protection


