
Ensures the security of Active Directory and blocks attack paths
There is an insecure Active Directory (AD) deployment environment behind each breach-related headline news. AD has become the favorite target of attackers; by exploiting known flaws and improper settings, attackers can escalate privileges and perform lateral movement.
Tenable.ad allows you to gain full visibility into Active Directory, predict the most critical issues, and take action to mitigate risks by searching for and fixing vulnerabilities in Active Directory before an attack occurs, thereby blocking attack paths.
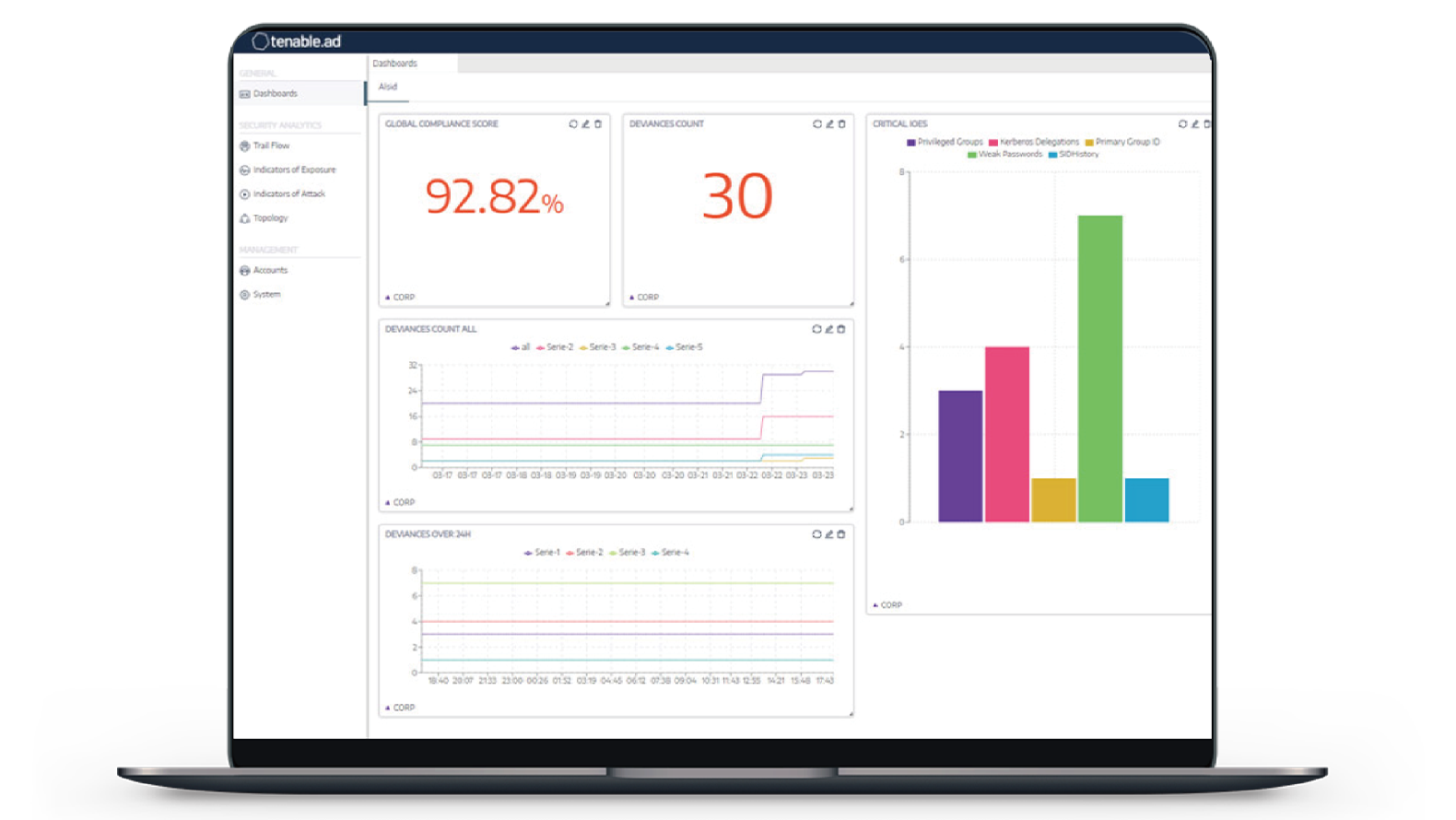
Tenable ad product features
Continually detects and prevents ACTIVE DIRECTORY attacks
-
01
No need for agent programs, no need for special permissions, No delays
No need for agent programs and special permissions to prevent and detect complicated Active Directory attacks.
-
02
Covers cloud
Real-time checking of Security of Azure Active Directory Domain Service, AWS Directory Service or Google Managed Service for Active Directory.
-
03
Deploy at any location
Tenable.ad provides flexibility with two different types of architectural designs. Internal deployment allows you to keep the data on-site and under your control. Software as a Service (SaaS) allows you to use the cloud.

Use Tenable.ot to disrupt OT threats
IT and OT environments are quickly blending. The physical isolation system times are over. Industries and key infrastructure enterprises are adopting Internet of Things (IoT) technology with unprecedented speed.
Although these new technologies generate high benefits and save a significant amount of cost, however, they are not without risks. Without comprehensive OT security measures, the vulnerabilities and medium of attacks will increase, causing unbearable risks.
Tenable.ot can protect industrial networks from cyber threats, malicious internal staff and man-made errors, ensuring the security and stability of the operating environment, and providing comprehensive visibility, asset management, configuration control, advanced threat detection and risk-based vulnerability management.
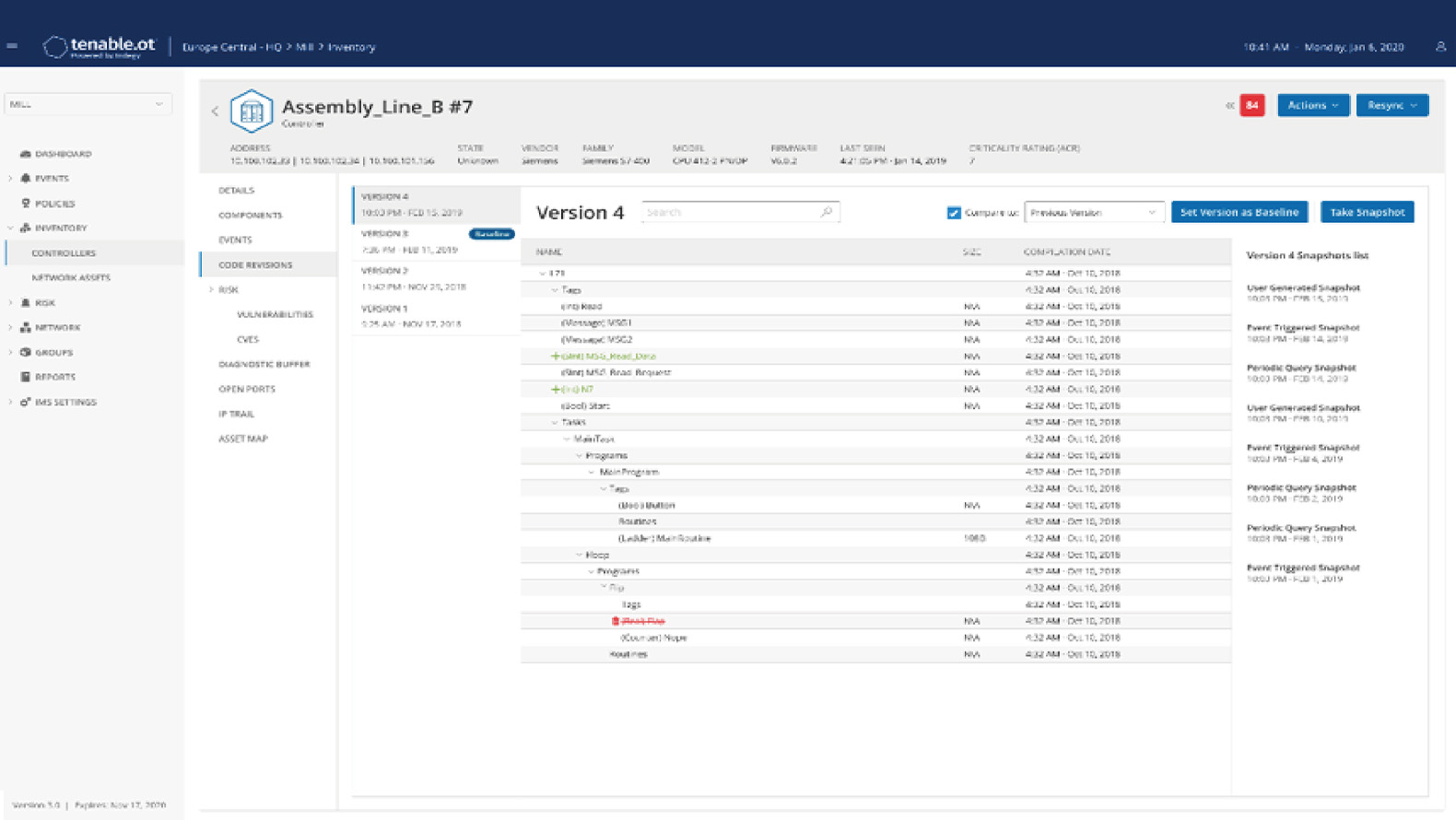
Tenable.ot can be integrated and used with Tenable.sc and Tenable.io.
[ Main features
Complete visibility and security, and controls the threats that may pose risks to your company
Tenable.ot can protect industrial networks from cyber threats, malicious internal staff and man-made errors. Tenable.ot can distinguish and defend operation technology (OT) environments, allowing them to avoid cyber exposure and threats, and ensuring the security and stability of operating environments.
-
01
Comprehensive visibility
Up to 50% of the OT infrastructure contains IT assets. Attacks can be launched across IT/OT infrastructures and easily be spread. Tenable.ot can provide enterprises with complete visibility for integrated attack vulnerabilities, while measuring and controlling the network risks of OT and IT systems. Tenable.ot not only can be integrated with Tenable product solutions, it can also be integrated with mainstream IT security tools on the market.
-
02
Asset management
Tenable.ot can allow enterprises to have an in-depth understanding of infrastructures, and provide unparalleled control for actual operation statuses without causing any impact on operations. The information collected by this patented method is far more than from passive monitoring; it includes identifying the network in your company and devices that are not actually performing communication.
-
03
Advanced threat detection
Attack mediums can find vulnerabilities in OT environments actively before attacks are launched. In addition, the multiple detection engines of Tenable.ot can identify situations that violate the policies, detect abnormal behaviors and track the signatures of potential high-risk incidents. The detailed controls allow your company to set and finetune detection methods to exert maximum performance with the method most suitable for your corporate environment. Through prompts with rich contents, you can quickly respond to and mitigate the threats that impact operations.
-
04
Risk-based vulnerability management
Tenable.ot fully applies their expertise in the industrial security field on OT assets, and fully applies Nessus on IT assets. The VPR scoring on Tenable uses every asset in the ICS network to generate vulnerability and risk levels. The report includes in-depth analysis and detailed insight, along with recommendations to mitigate risks. This allows authorized personnel to quickly find the highest risk and patch them in the order of importance before the vulnerabilities are exploited by attackers.
-
05
Configuration control
By using Tenable.ot, your company can track malware and allow users to make changes to the execution of devices directly through the Internet. Tenable.ot provides complete historical records of changes in device configuration over time, including detailed information such as specific ladder logic sections, diagnostic buffers and tag table, etc. This way, administrators can back up snapshots to create the “final correct status” to restore more quickly and comply with industrial laws and regulations.
World’s #1 Cybersecurity Risk and Vulnerability Management Platform

Tenable.sc provides highly customizable vulnerability analysis, trend tracking, reporting, and workflows to meet the needs of your security plan.
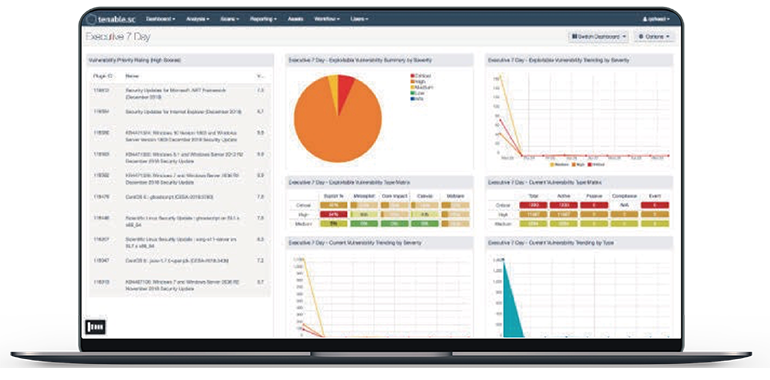
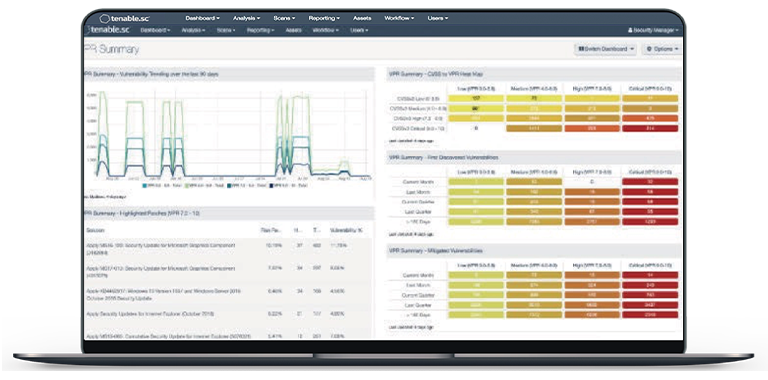
Key Features
-
01
Identifies weaknesses such as vulnerabilities, misconfigurations, and malware through scanning connected assets.
-
02
Prioritizes the most impactful vulnerabilities and predicts the likelihood of specific vulnerabilities being exploited in the next 28 days.
-
03
Quickly identifies which vulnerabilities should be patched first to minimize risk, allowing you to focus on the most critical areas.
-
04
Simplifies compliance with various regulations/IT standards and best practices.

Cloud-native application protection platform (CNAPP)
Tenable.cs is a cloud-native application protection platform (CNAPP); it can allow your information security team to define the policy as code (PaC) that your team can apply at the construction stage and execution stage, and extend the vulnerability management function to the cloud workload.
Tenable.cs shortens the gap between traditional security operations and cloud development teams by building on the foundation of Terrascan; Terrascan is one of the most popular open source Infrastructure as Code (IaC) cloud security testing tools on the market.
By using Tenable.cs, you can reduce the number of threats to repair during the execution stage by incorporating security tasks in advance, and treat the solving of security vulnerabilities as part of the development process.
Main Features
Cloud Security as Code
Tenable uses the five major elements of Cloud Security as Code to help you establish and strengthen DevSecOps practices:
-
01
Policy as Code
Continuous Assessment
Understand security policies as code (such as CIS indicator analysis), continuously detect violations of policies throughout the entire Infrastructure as Code (IaC) during the construction phase, and enforce security policies early before deployment (CI/CD).
-
02
Governance as Code
Automate Governance
Manage security governance decisions within IaC (e.g., exceptions) and use code repositories for governance workflows and auditing.
-
03
Drift as Code
Continuous Detection
Continuously detect changes in the infrastructure during the execution phase and report violations of IaC principles.
-
04
Security as Code
Advanced Security
Understand application vulnerabilities, identify potential leak paths, and assess impact to prioritize risk mitigation strategies.
-
05
Remediation as Code
Automated Remediation
Automatically generate IaC code to fix vulnerabilities and exposures. Push security fixes directly to developers through GitOps requests with IaC.
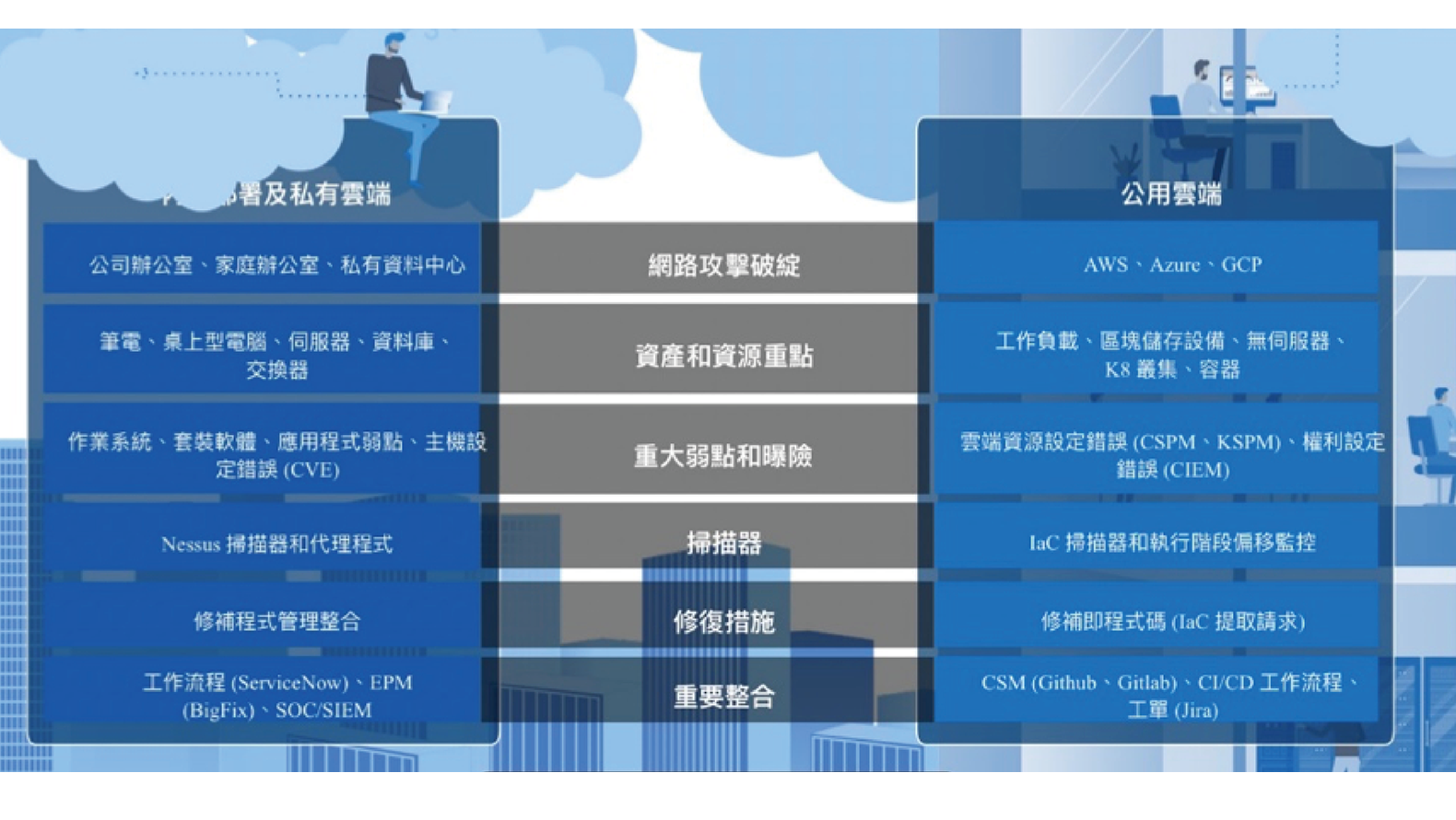
The Core Vulnerability Management Function Must Be Extended to the Cloud
No need to install agents, configure scans, or manage credentials—continuously search and assess cloud assets. Gain deep visibility into the security posture of your container images. Quickly detect security issues as new vulnerabilities are disclosed and as your cloud environment changes due to instances evolving.
Functions designed specifically for developers
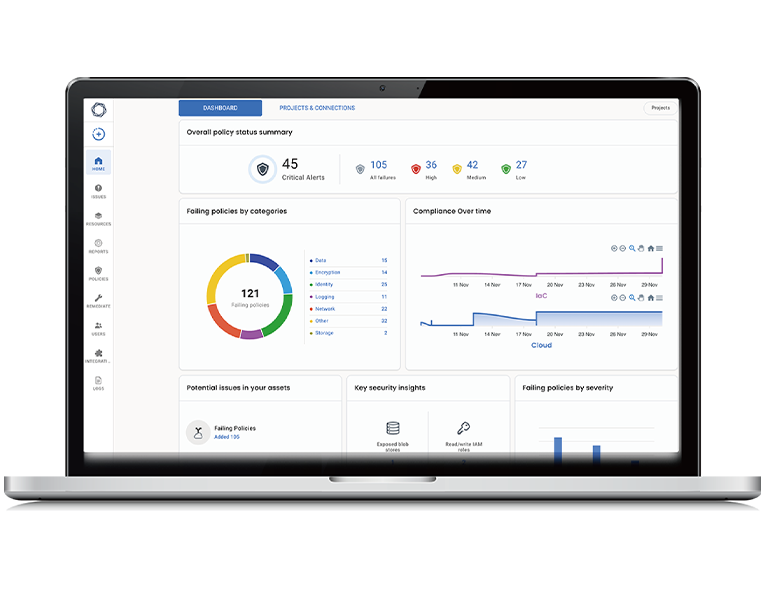
- Integrate Tenable.cs into your IDE to continually check security syntaxes in your Infrastructure as Code.
- Create Infrastructure as Code snippets automatically from an executing cloud setting.
- This saves time and effort since every approval adheres to defined security policies.
- Integrate assessments and findings into tools you know and trust, including: Github, Gitlab, Jenkins, Slack and Bitbucket, etc.
- Tenable.cs is built on Terrascan; this is an open source IaC security testing tool provided for developers to use for free.




